Ensure IT Compliance While Saving Time and Resources
Demonstrate your commitment to information security and privacy compliance. Maintain certifications that improve your security posture and reduce the risk of a costly data breaches while building trust with customers and the public. Work from a centralized system that streamlines efforts and provides clear visibility into your compliance program.
Manage Your Security Certifications
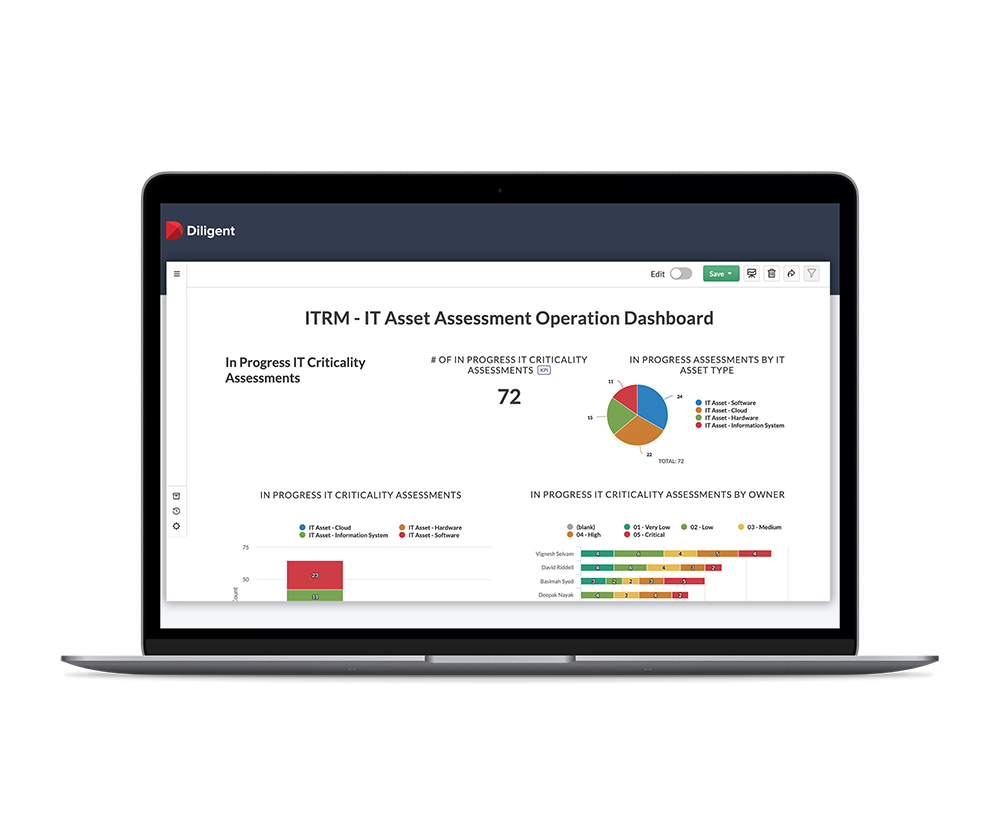
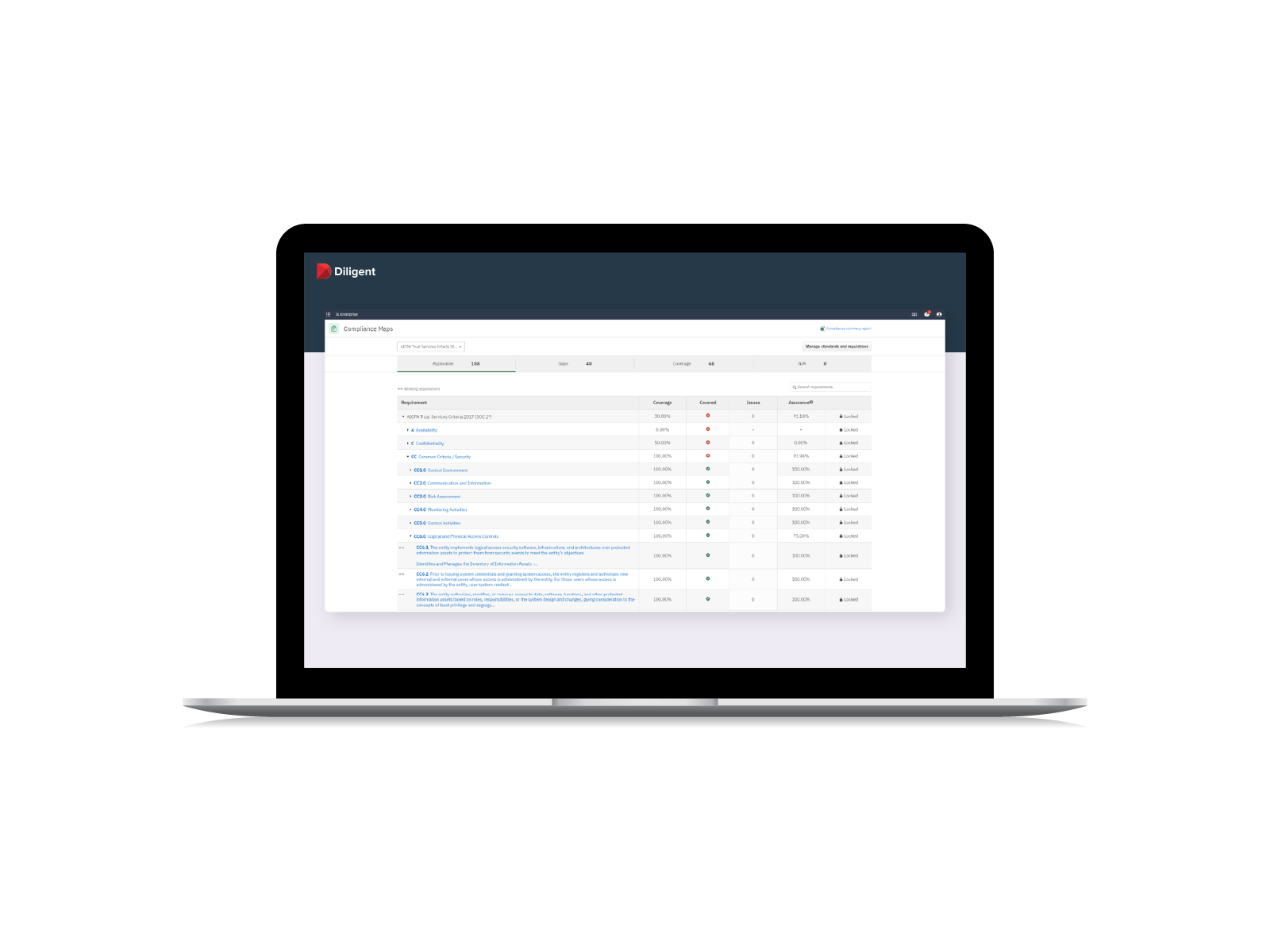
With out-of-the-box capabilities, we enable IT teams to manage and monitor compliance for 75+ standards, guidelines, frameworks, and regulations.
Centralize IT Compliance Into a Single System
Automate your security compliance program from a centralized, single source of truth for better efficiency, scalability, and executive visibility.
- Deliver a robust IT compliance program that meets the frameworks relevant to your organization, including HIPAA, ISO 27001 / 27002, NIST 800-53 FedRAMP, NIST-800-171, PCI, SOC2 and 75+ more
- Scale up to cover additional frameworks that open new revenue segments using a single system of record
- Democratize assessments by automating the delegation of evidence collection to control owners
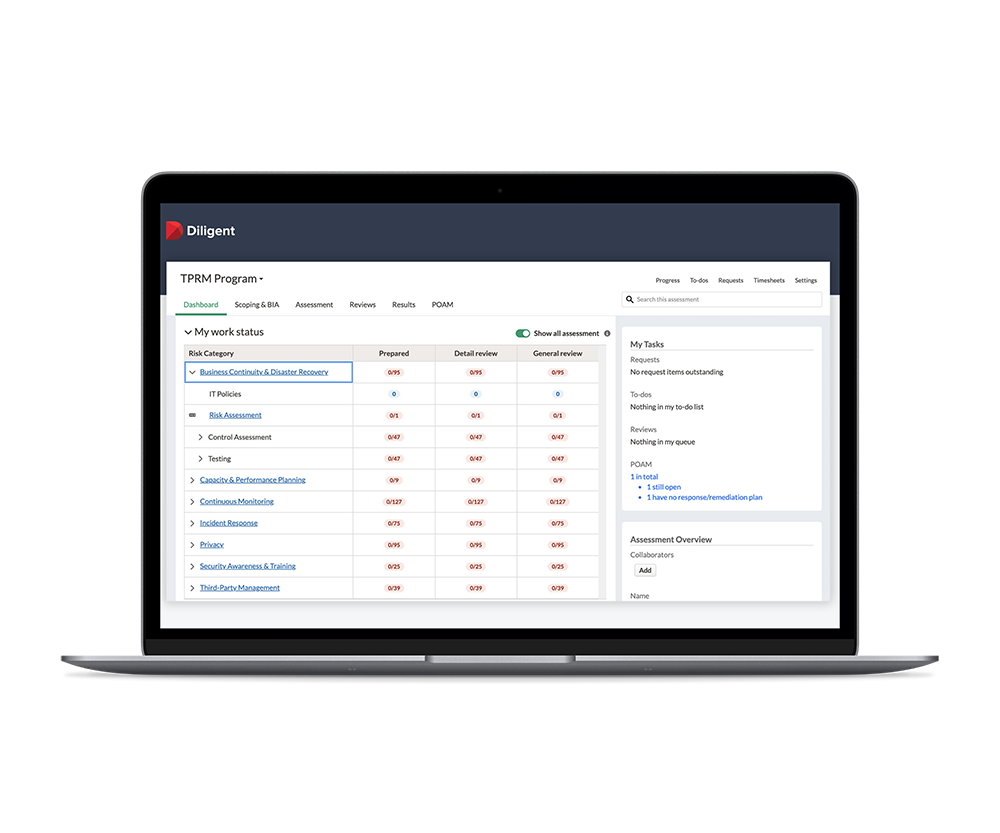
- Manage your program and facilitate audits – both internal and external – all from the same system
- Save time preparing for committee meetings with ready-to-use reports that deliver an aggregated view of certifications to reassure the board and C-suite
Save Time and Resources With Automated Workflows
Increase the efficiency of your IT compliance program so you can reclaim time for more strategic initiatives.
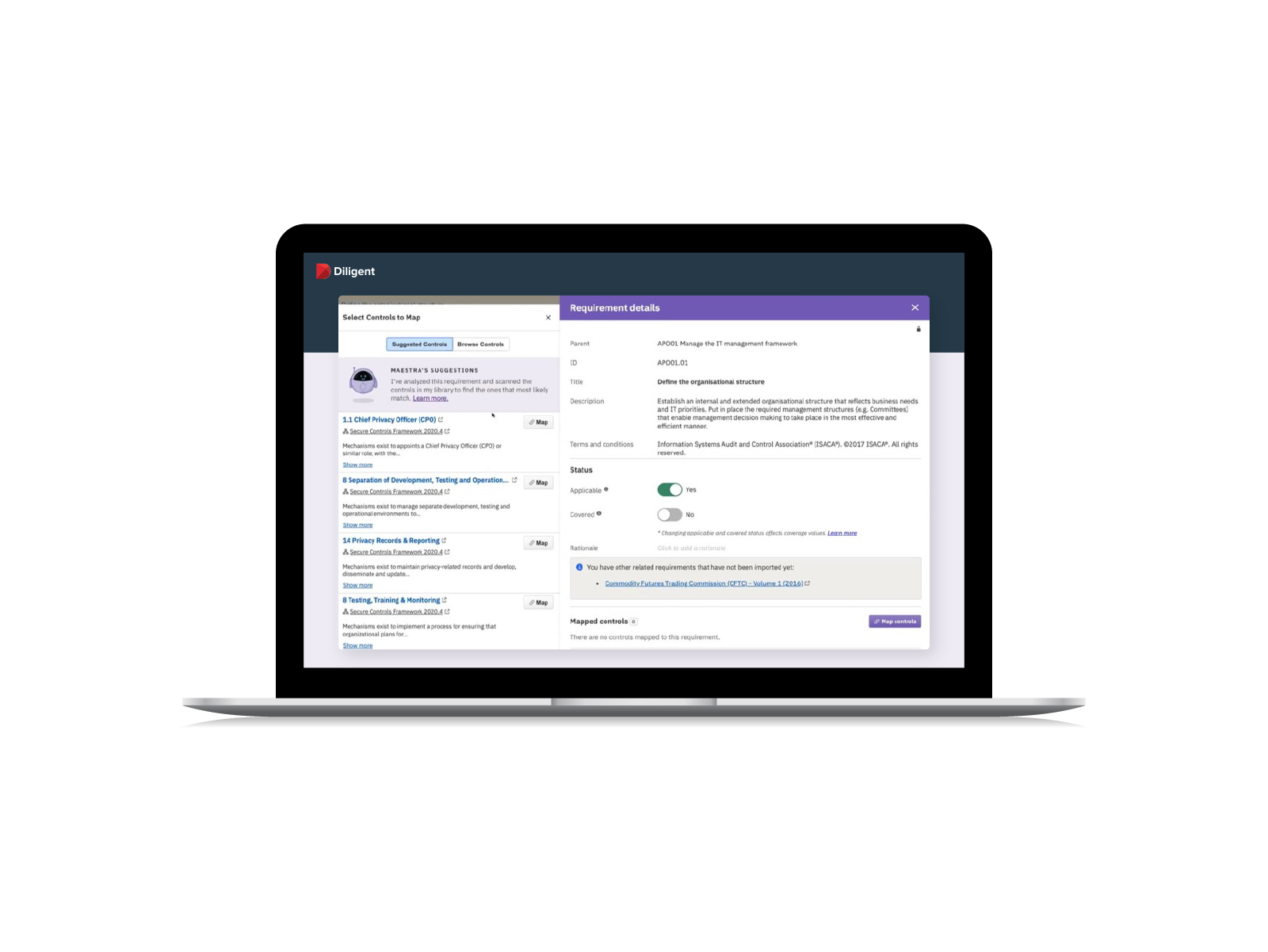
- Leverage pre-built requirements, controls and mapping built by our in-house experts
- Use an AI engine to accelerate mapping controls to multiple relevant security requirements, saving time and improving accuracy
- Replace repetitive, manual efforts with automated surveys, remediation and centralized evidence collection for audit-readiness
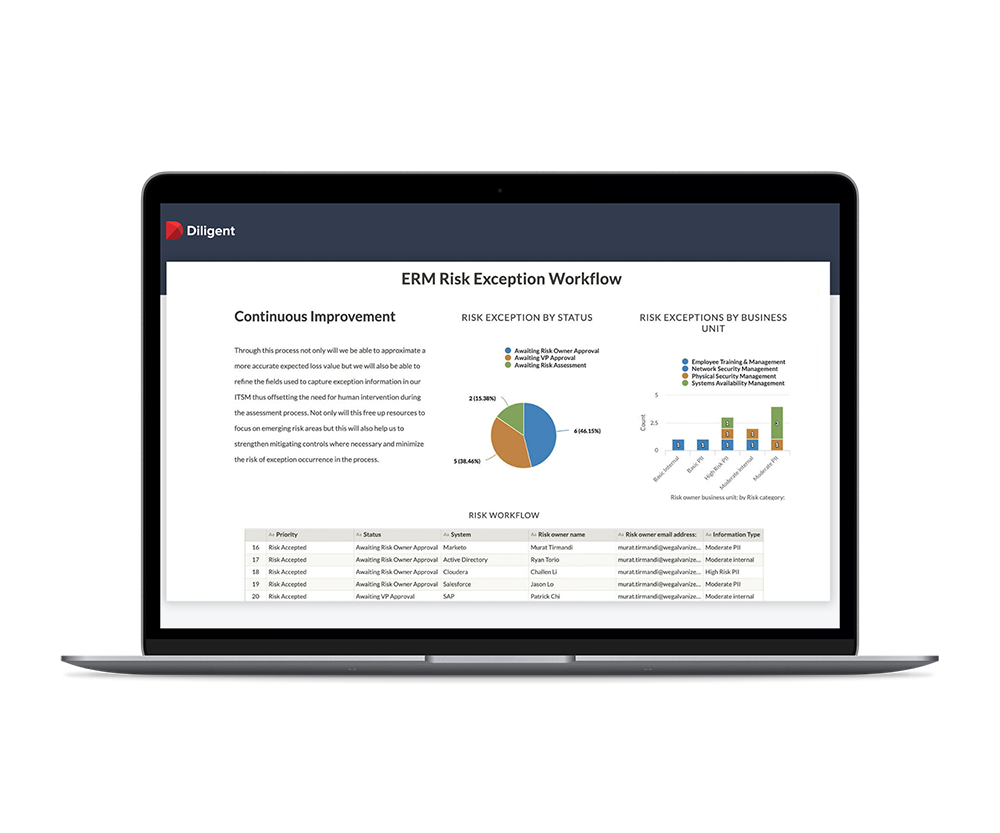
Protect Your Organization with Continuous Controls Monitoring
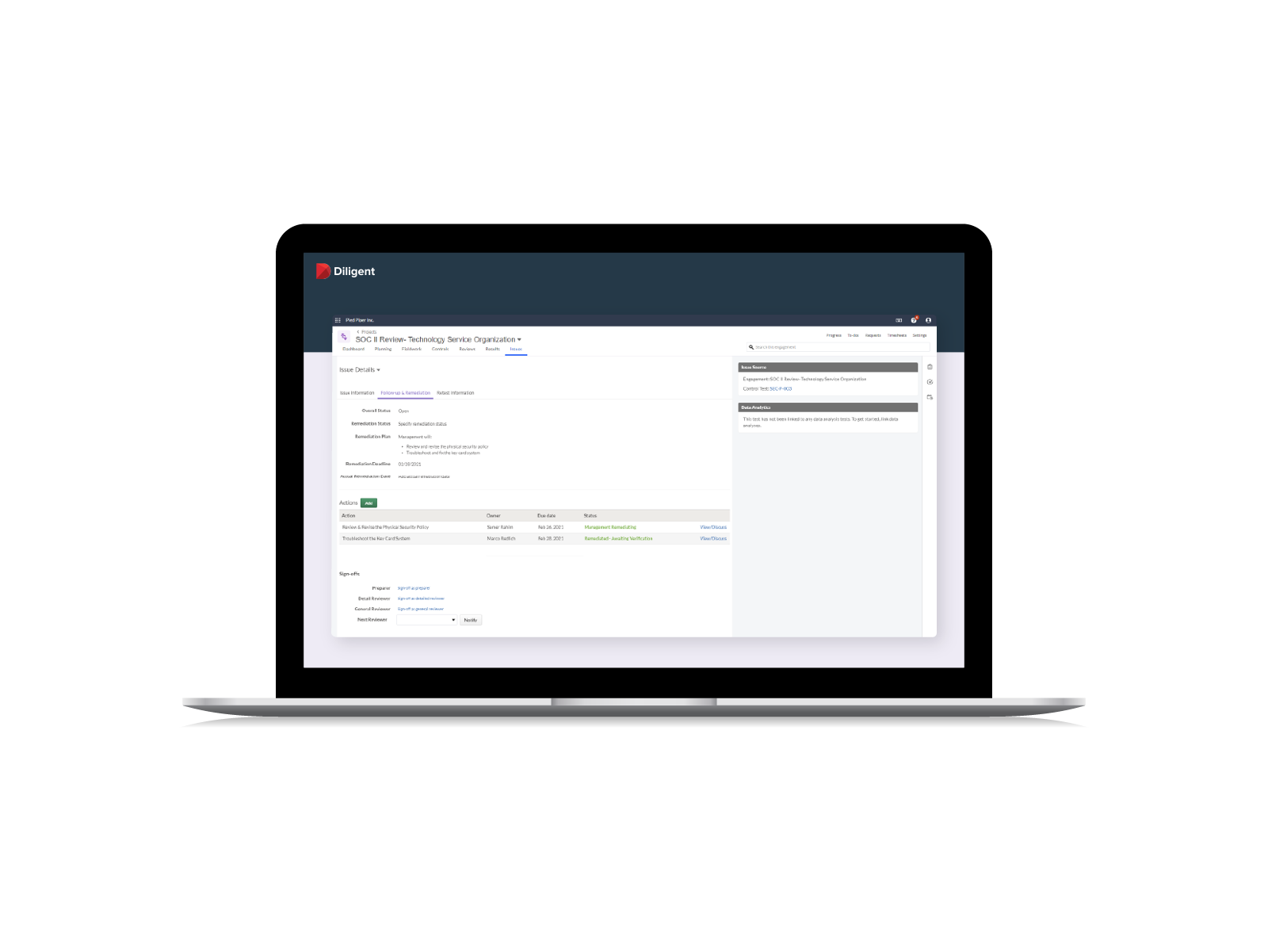
Controls are only useful if they are properly adhered to. Lower the likelihood of a breach with in-depth, continuous controls monitoring.
- Move beyond a checklist approach to continuously monitor critical controls
- Identify and quickly remediate issues, such as user access and segregation of duties
- Proactively manage your IT compliance program to ensure continuous compliance
Related Insights and Resources






RESPONSIVE
24/7/365
Award-Winning-Support
1,500+
Dedicated Employees
TRUSTED
25,000+
Customers
1,000,000
Users
IMPACTFUL
700,000+
Board Members & Leaders
130
Countries
Speak with an expert advisor to arrange a custom demo
See how can we help you drive success with a demo customized to your workflow and business objectives
“Not only is the training great, but the tool’s capabilities are fantastic and will lead to several process efficiencies and opportunities.”
Manager, IT Service Management & Compliance