Common Data Storage Types
The type of data stored in our system commonly includes: risks, controls, and policies related to the organization or public sector entity at both a strategic or enterprise level and process or
- location level
- testing of design and effectiveness of risks, controls, and policies
- exceptions and issues related to the testing & integrating relevant data analytics related to transactional data sampling or monitoring.
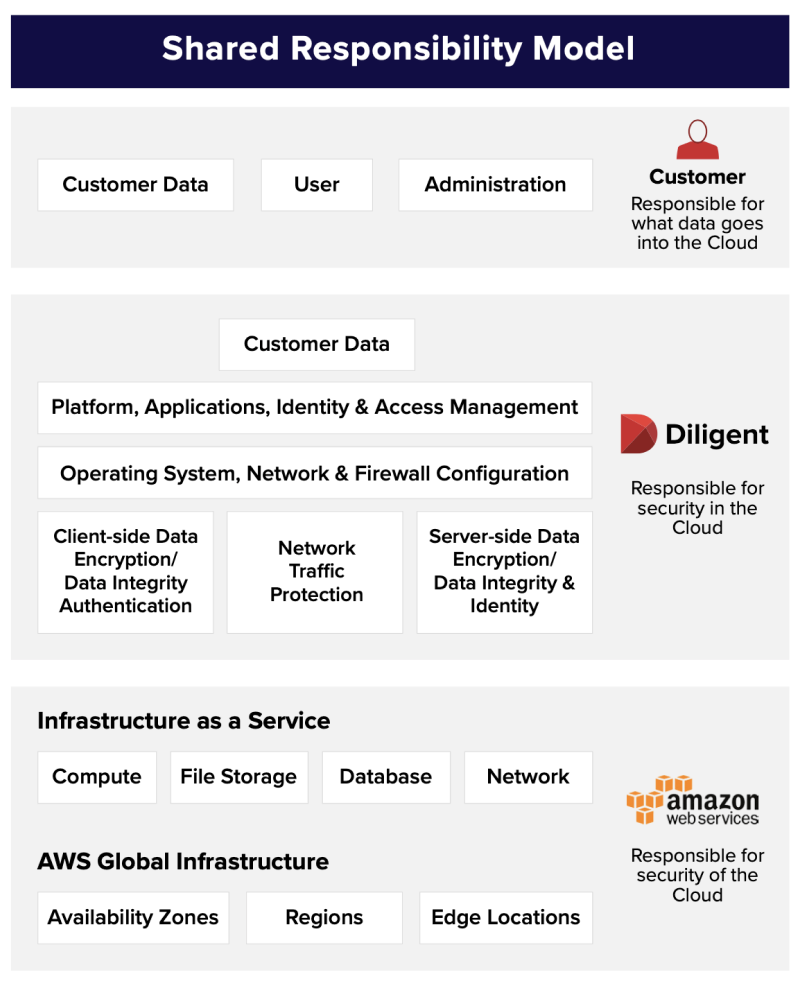
Shared Responsibility Model
Diligent manages the overall application infrastructure and our customers manage the end-user security and access control to their individual system. This is known as the Shared Responsibility Model, which is comprised of:
- Customer responsibility
- Diligent responsibility
- Amazon Web Service (AWS) responsibility
Customer Responsibility
Customers share the responsibility of not only keeping their data secure, but also complying with applicable regulatory or privacy laws. Our customers have full ownership of their user access controls and manage their entire data lifecycle from deciding what data goes into the system, how long it should be retained, what data should be deleted, and whom can access the data.Customer environment access
Our customers should have controls in place to restrict access to the individuals to whom account access is required. Controls should include approving individuals for access to accounts prior to setting up users in the system and revoking users’ log-in credentials when user access is no longer required or if user authentication credentials or other sensitive information has been compromised. HighBond includes several capabilities to assist customers in their responsibility to manage end-user system access, including the ability to:- Enforce strong passwords
- Configure password expiry
- Configure session timeout
- Configure SSO (Single-Sign On) via SAML 2.0
- Lock user accounts after multiple failed log-ins
- Easily delete or suspend user accounts
- Specifically identify permissible user IP addresses
- Use activity tracking to log access and system use
Diligent Responsibility
In addition to the physical and hardware security that Amazon provides, we also have a robust information security environment to ensure that the confidentiality, integrity and availability of customer data meets our high standards and our customers’ high expectations.Amazon Web Services (AWS) responsibility
Amazon is the largest vendor of data storage and computing on the planet, and they are responsible for the physical facility as well as the physical infrastructure of server hardware, networking, and related services for the HighBond service and hosting customer data.Data Encryption
We provide strong encryption of all data in transit and at rest. Encryption in transit is achieved via the industry- standard TLS (Transport Layer Security) protocol supporting only the strongest encryption algorithms, including AES (Advanced Encryption Standard) with up to 256-bit key lengths. Encryption at rest is achieved by leveraging AWS storage encryption, using AWS KMS to create and store the 256-bit AES encryption keys.About encryption
By using TLS version 1.2, an encrypted communication channel between the end-user web browser and the HighBond service is established, ensuring the confidentiality and integrity of all data transmissions from end-to-end.The AES encryption algorithm is widely recognized and approved by organizations worldwide as an industry standard in government, military, and commercial applications.
AES-256 bit TLS encryption is supported on most browsers. If your browser does not support AES-256 bit TLS encryption, you will not be able to access the HighBond service and all related components.All emails from our platform are transmitted via TLS- encrypted channels, when available. If the recipient’s email server does not support TLS, emails are delivered over the default unencrypted connection.
Hashing function
If and when customers choose to publish data to Results for evidence as part of control testing, or for further review as part of risk mitigation, ACL Analytics and Analytics Exchange both include a hashing function for customer end-users to apply to any sensitive data fields, such as:- patient records
- social security identifiers
- credit card numbers
- bank or mortgage account numbers
- payroll
- criminal activity
Passwords
User passwords are never stored. A strong cryptographic algorithm is used to generate irreversible strings known as password hashes. The stored hashes are without any value to an adversary even if obtained. The algorithm uses a unique long random value known as a salt, which is different for each user and ensures protection against attacks based on pre-computation of password hashes.Password expiry
Password expiry is a security feature that limits unauthorized access to our service. If you are using password expiry, consider the following:- Account Admins can enable password expiry under Settings > Update Organization in Launchpad.
- Password expiry is configured as the number of days between password changes.
- Note: The minimum duration supported for password expiry is 7 days. There is no maximum duration.
- If your password expires, one or more organizations you belong to have enabled password expiry.
- Your password expiry is based on the shortest expiry length of all the organizations you belong to.
- You will receive a notice in Launchpad one week prior to your password expiring.
- If your password expires, you will need to reset your password to sign in to Launchpad.
Password complexity
Our service includes a security setting that determines whether passwords meet complexity requirements. Complexity requirements are enforced when you change or reset your password in Launchpad. Passwords must meet the following requirements:- Passwords must be a minimum of 8 characters in length
- Passwords must include at least one lower case, one upper case, and one numeric character.
- Note: Passwords may contain special characters.
- You cannot re-use any of your last five passwords as your new password.
Password attempts
When signing in to our platform or generating a token to use in another application, you have up to five attempts to enter your password. After five attempts, reCAPTCHA displays. reCAPTCHA is a service that protects websites from spam and abuse, and requires you to enter a series of characters or numbers to prove you are human.Session expiry
A session is a period of activity between a user logging in and out of an application. Sessions are global to all HighBond SaaS modules, which means you use the same login session whether you are in Strategy, Projects, Results, or Reports. Your session expires if you are inactive for the duration of time set by an Account Admin. Note: Session expiry does not apply to the mobile app, ACL Analytics, or Analytics Exchange. When a new organization is created, the default session timeout is set to 60 minutes. If users have access to more than one organization, their session will expire as per the shortest session expiration time limit set across all their organizations. If you are using session expiry, consider the following:- Account Admins can enable session expiry under Settings > Update Organization in Launchpad.
- Session expiry is calculated by the number of minutes that a browser session remains inactive.
- The minimum duration supported for session expiry is 15 minutes and the maximum is 30 days.
- You can have multiple tabs open at one time in one browser as each tab or window belonging to the same browser on the same machine shares the session.
- You can use a maximum of two concurrent sessions in different browsers. If you log in from a third browser, the oldest session is expired.
- You can log in with either the same user or different users on different browsers or machines, and logging out of one will not log you out of the others.
- Your session expiry is based on the shortest expiry length of all the organizations you belong to.
IP Restrictions
IP restrictions allows organizations to configure one or more IP (Internet Protocol) addresses or IP address ranges from which a user may access the organization. IP restrictions may be used as an additional factor in multi- factor authentication, in addition to password credentials, to ensure only authorized users access the organization. IP restrictions only impacts our applications when they interact with Cloud data, including:- Exporting results from Results to ACL Analytics
- Importing results from ACL Analytics to Results
- Using scripts to export results from Analytics Exchange to Results
- Publishing results from Add-In for Excel to Results
- Importing tables from Projects to ACL Analytics
- Checking in or checking out sections in the mobile app or Projects client
- Uploading Excel worksheets from ACL Add-In for Excel to Projects
- Account Admins can configure IP restrictions under Settings > Update Organization in Launchpad. Note: In order to prevent Accounts Admins from locking themselves out of our service, Account Admins are unable to configure an IP address that does not comply with their current IP address.
- If the IP allow list has any IP addresses or IP address ranges defined, only users whose IP addresses match the IP allow list may access the organization.
- All users accessing Cloud data within a specific organization are subject to IP restrictions.
- Users belonging to multiple organizations must comply only with the IP allow list of the organization they are currently accessing.
- If an IP allow list is enabled, users on mobile devices or public networks with dynamic IP addresses cannot comply with their organization’s IP allow list.